Disaster Management and Contingency
Summary and Value Proposition
Business continuity and disaster recovery (BC/DR) planning begins with a thorough risk assessment. Risk assessment is part of a larger risk management process found in most businesses. The four major components of the BC/DR risk assessment are threat assessment, vulnerability assessment, impact assessment, and risk mitigation strate
gy development.
In this article , we focus on threat and vulnerability assessment. In order to perform a thorough threat assessment, you need to look at threats and threat sources both internal and external to the company. It is often helpful to assess risk based on the potential risks to people, process, technology, and infrastructure.
People are not only the company’s employees but also its vendors, partners, customers,
and the larger community in which it operates. Processes are all the business
and IT processes used in the business. Processes are used to generate revenue, track
expenses, and manage operations from facilities management to human resources
and beyond.
From an IT-centric viewpoint, the key components to address in the risk assessment
are people, process, technology, and infrastructure. It includes hardware,
software (OS and applications), system interfaces (internal, external connection
points), people who support the IT systems, users who use the IT systems, data, information
and records, processes performed by the IT systems, system’s value or importance
to the organization (system criticality), and system and data sensitivity
(confidential, trade secret, medical data, etc.). The operating environment in which
the IT systems function includes a wide variety of elements. Among them are the
functional and technical requirements of the systems; security policies, procedures,
and controls; network topology and information flow diagrams, data storage protection
policies, procedures, and controls; encryption, physical, and environmental
controls.
Analysis of the Situation
The methods used to gather data for any of the assessment phases typically
include questionnaires, interviews, document reviews, and research. Questionnaires
not only can be helpful in structuring desired input but also can have the downside of
containing built-in biases, often unintentionally. Interviews can be conducted with
subject matter experts and yield more useful information than questionnaires but
may also generate a lot of tangential or unneeded data. Reviewing documents and
performing research can supplement the questionnaire and interview process.
Once you’ve defined the methods you’ll use to gather the necessary data, you can
begin your review of various threats. We discussed many different types of threats
that fall into three primary categories: natural and environmental threats, human caused
threats, and infrastructure threats.
Infrastructure threats are caused by either natural or human causes, and it’s important to delineate these because they involve people, processes, and technologies outside the company and the company’s control.
As such, they sometimes can be overlooked in IT BC/DR planning. Natural threats
include those we might commonly think of such as fire, flood, or earthquake, but we
also discussed other less obvious threats including volcanoes, droughts, and pandemics.
Human-caused threats can be intentional as in the case of terrorism, labor
disputes, or workplace violence, or they can be unintentional as can be the case with
fire, flood, or a security breach. Infrastructure threats include those to the building as
well as external to the building and the company. Public transportation including
roads, rails, seaports, and airports are all external infrastructure elements that need
to be assessed. Other external elements include threats to water and food supplies,
biological and chemical hazards, and public utilities such as the power grid, petroleum
and fuel supplies, or telecommunications.
Threat Assessment
The threat assessment methodology begins with a list of all potential threats and
threat sources. Each threat source is then evaluated. Some people like to assess likelihood
of occurrence and vulnerability to the threat; others prefer to include both likelihood
and vulnerability in a single assessment. Regardless of whether you choose to
break them into two distinct ratings or one rating, the likelihood of occurrence and
vulnerability rating(s) should be assessed for each threat source. The argument for
making two separate assessments is that a threat may have a high likelihood of occurring,
but your company and its people, processes, technology, and infrastructure may
not be vulnerable to those threat sources. Others would argue that if there is a
therefore not be assessed separately. Either method is acceptable as long as you make
a conscious decision as to how to proceed and use the same process throughout your
risk assessment cycle.
Qualitative Assessment
You can perform a quantitative assessment in which actual values such as dollars
or frequency are known. The benefit to this type of assessment is that you can generate
hard data that can be used in a standard cost/benefit analysis. The downside is
that not all values are easy (or possible) to derive, and an unacceptable amount of
time or money may be required to generate that data. You can also perform a qualitative
assessment in which values are relative. These types of assessments use labels
such as high, medium, and low or an arbitrary numbering system such as 1-100 where
1¼no chance or extremely low, 50¼medium chance or about average, and
100¼will occur or extremely high chance. These kinds of systems are much easier
to implement but typically generate less specific data that are unsuitable for a standard
cost/benefit analysis. In analyzing threat data, qualitative measurements are
often sufficient to generate a clear picture of the threats facing the organization.
The vulnerability assessment may include the likelihood of occurrence or it may
be a separate rating. However, the same processes can be used to evaluate vulnerability
as were used to assess threats. Questionnaires, interviews, document reviews,
and research can help in generating data needed to assess the actual or relative vulnerability
to a threat. This rating is compiled with the threat assessment data and is
used as the input to the BIA phase.
The Bottom Line
The bottom line is that your risk assessment activities will end up, generating a
list of threats and threat sources that you’ll be able to evaluate. You can sort the list
and decide which risks you need to address, which can be accepted, and which should
be transferred. You’ll have the data to make this decision once you complete the BIA,
the third major step in the risk assessment process.
BC/DR Operations Management
BC/DR is the Process of Planning and Implementation of disasters caused by natural phenomena and or man made situation. It is interesting to note that 90 % of small and medium business cease of exist after 2 years , if they did not have written BC/DR plan in place[3]. Large Business in US and Canada also have Legal and financial implications of safeguarding taxation and revenue data.
Planning and execution of BC/DR requires knowledge of operations management and contingency analysis. IT Network Management plays a crucial role in planning recovery phase of the BC/DR process. Six sigma, Lean and Agile Process are used in many occasions.
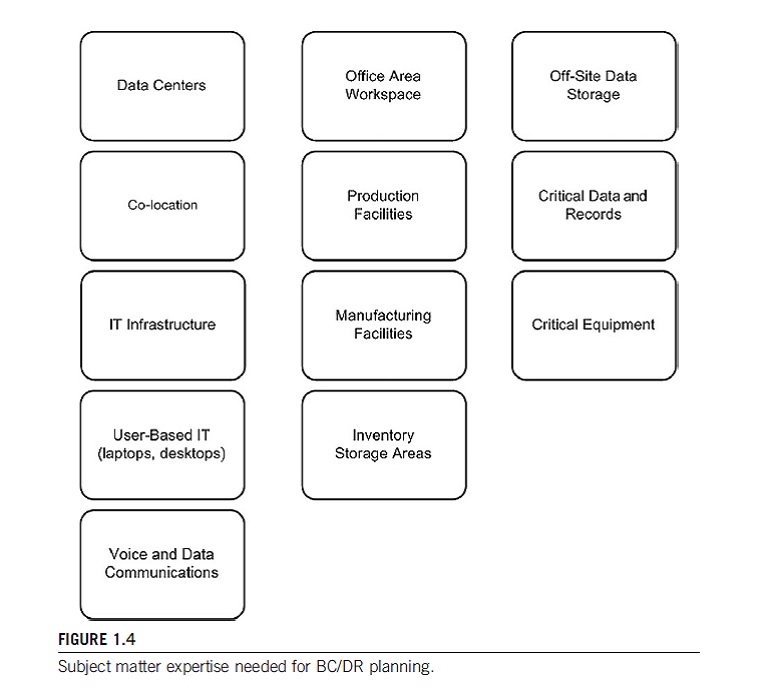
Figure 1.4 shows the subject area expertise that is needed to implement BC/DR process of an organization. As shown in figure 1.4 BC/DR calls for diverse expertise on the part of the organization. It is due to this reason sometimes external technical help is sought.
In BC/DR the following points must be accessed by the operations manager and CEO of an organization
- Cost of planning verses the cost of failure
- Business impact analysis
- Legal and Regulatory Obligations- , shareholders and taxation department- stolen credit card number is an example.
- BC/DR Project management and analysis of operations management
- Risk Assessment
- IT and Physical infrastructure threats
- BC/DR in health care and emergency services
- Risk mitigation strategy development
- IT Risk Mitigation- backup and recovery, cloud based solutions as an alternative.
- Communicating and receiving input on all stakeholders
- Agreement on the level of acceptable risk.
- Emergency response and recovery procedure
- Assignment of chief BC/DR coordinator
- Training testing and auditing BC/DR process
In a public organization like municipality, school, hospital , you are legally obligated to maintain and enact a BC/DR plan. However in small business and corporations you have legal obligations from shareholder and revenue collection agency. Simply saying you have lost all your financial data due to natural disaster and IT disaster is not acceptable.
BC/DR Needs to be continually tested, audited and checked for validity. As the organization grows, the outdated BC/DR will not work properly of the contingency plan is not updated accurately.
We at Keen Computer designs business continuity and disaster recover plan for your Organization. Please contact one of the subject area experts to discuss the possibilities.
References:
1.0 Eight Ingredients of Enterprise Recovery Plan- http://www.cio.com/article/3090892/disaster-recovery/8-ingredients-of-an-effective-disaster-recovery-plan.html
2.0 IT Disaster Recovery Plan- https://www.ready.gov/business/implementation/IT
3.0 Business Continuity and Disaster Recovery for IT Professionals, Second Edition- ISBN-13: 978-0124105263