Small and Medium Enterprises (SMEs) increasingly depend on digital platforms for sales, customer engagement, internal operations, and remote collaboration. However, the network infrastructure supporting these digital initiatives is often under-designed, insecure, and poorly managed. Consumer-grade ISP gateway devices, flat network topologies, weak wireless coverage, and unmanaged switching remain common in SME environments across India, Canada, the USA, and the UK. These limitations directly impact business performance through security incidents, poor VoIP call quality, downtime, limited scalability, and reduced readiness for cloud and AI-driven services.
This white paper proposes a professional, reference network architecture for SMEs based on: (1) ISP modem in bridge mode, (2) dedicated firewall/router for security and DHCP, (3) managed Power-over-Ethernet (PoE) switches with VLAN segmentation and Quality of Service (QoS), (4) centrally managed Wi-Fi mesh or access point systems, and (5) VoIP telephony integrated with traffic prioritization. The paper further situates this architecture within a cybersecurity and managed network services framework, highlighting the role of service partners such as KeenComputer.com in designing, implementing, and operating resilient SME networks.
Designing a Secure, Scalable SME Network Architecture with Bridged WAN Modem, Firewall Router, Wi-Fi Mesh, Managed Switches, VoIP, and Cybersecurity Management
A Professional Research White Paper for SMEs in India, Canada, USA, and the UK
Prepared for: SME Owners, IT Managers, Digital Transformation Leaders
Prepared by: KeenComputer.com | IAS-Research.com
Year: 2026
Abstract
Small and Medium Enterprises (SMEs) increasingly depend on digital platforms for sales, customer engagement, internal operations, and remote collaboration. However, the network infrastructure supporting these digital initiatives is often under-designed, insecure, and poorly managed. Consumer-grade ISP gateway devices, flat network topologies, weak wireless coverage, and unmanaged switching remain common in SME environments across India, Canada, the USA, and the UK. These limitations directly impact business performance through security incidents, poor VoIP call quality, downtime, limited scalability, and reduced readiness for cloud and AI-driven services.
This white paper proposes a professional, reference network architecture for SMEs based on: (1) ISP modem in bridge mode, (2) dedicated firewall/router for security and DHCP, (3) managed Power-over-Ethernet (PoE) switches with VLAN segmentation and Quality of Service (QoS), (4) centrally managed Wi-Fi mesh or access point systems, and (5) VoIP telephony integrated with traffic prioritization. The paper further situates this architecture within a cybersecurity and managed network services framework, highlighting the role of service partners such as KeenComputer.com in designing, implementing, and operating resilient SME networks.
1. Introduction: SME Digital Transformation and the Centrality of Network Infrastructure
Digital transformation has become a defining strategic priority for SMEs. Websites, ecommerce platforms, cloud-based accounting, customer relationship management (CRM) systems, AI-powered marketing tools, and remote collaboration platforms are now core to business operations. Despite this dependence, many SMEs continue to rely on network infrastructures originally designed for home or micro-office use.
In practice, this results in:
- Overloaded ISP gateway devices performing modem, router, firewall, and Wi-Fi roles simultaneously
- Flat networks without segmentation between business systems, guest access, and voice traffic
- Poor wireless coverage and roaming performance
- Inconsistent VoIP call quality
- Weak cybersecurity controls and limited monitoring
These limitations translate into measurable business risks: customer dissatisfaction due to dropped calls, productivity losses from unreliable connectivity, regulatory exposure due to weak data protection controls, and increased vulnerability to ransomware and phishing attacks. As SMEs expand into ecommerce, adopt AI tools, and support hybrid work models, the network becomes not merely an IT utility but a strategic business asset.
This paper argues that a modular, segmented, professionally managed SME LAN architecture provides a practical pathway to digital resilience and growth.
2. Limitations of ISP All-in-One Gateways
ISP-provided gateway devices are optimized for cost efficiency and ease of deployment rather than business-grade performance and security. Key limitations include:
- Limited firewall rule granularity and logging
- Absence of VLAN support in many consumer devices
- Weak Wi-Fi coverage and poor roaming
- Inadequate QoS for real-time applications such as VoIP and video conferencing
- Restricted administrative access and vendor lock-in
From a systems perspective, combining modem, router, firewall, and Wi-Fi access point functions into a single low-cost device introduces a single point of failure and constrains architectural flexibility. When SMEs attempt to scale—by adding more users, VoIP phones, access points, or cloud services—the gateway becomes a bottleneck.
3. Bridge Mode WAN Modem: Establishing a Clean Network Edge
3.1 Concept of Bridge Mode
Bridge mode configures the ISP modem to operate as a Layer 2 device, passing the public IP address directly to the SME’s firewall/router. Routing, NAT, DHCP, and security policies are handled exclusively by the organization’s own equipment.
3.2 Architectural Benefits
Placing the modem in bridge mode provides:
- Elimination of double Network Address Translation (NAT), simplifying VPN and VoIP deployments
- Full control over firewall policies and security posture
- Improved troubleshooting and observability
- Decoupling of ISP infrastructure from internal network design
From a governance perspective, this establishes a clear demarcation point between external connectivity (managed by the ISP) and internal digital infrastructure (managed by the SME or its service partner).
4. Firewall Router as the Security and Control Plane
The firewall/router becomes the central policy enforcement point of the SME network. Core functions include:
- Stateful firewalling and intrusion prevention
- DHCP services for multiple VLANs
- Routing between network segments
- VPN termination for remote users and branch offices
- Traffic shaping and QoS
- Centralized logging and alerting
Adopting a dedicated firewall/router supports movement toward Zero Trust principles, where network access is explicitly controlled and monitored rather than implicitly trusted based on location.
5. Managed Switching, VLAN Segmentation, and Network Design
5.1 VLANs as a Security and Management Primitive
Virtual LANs enable logical segmentation of traffic across a shared physical infrastructure. For SMEs, VLANs offer:
- Isolation of guest Wi-Fi from business systems
- Separation of VoIP traffic to enable QoS and security controls
- Reduced broadcast domains, improving performance
- Simplified policy enforcement at the firewall
5.2 Role of Managed PoE Switches
Managed switches provide the capability to:
- Assign VLANs to ports
- Prioritize voice traffic using 802.1p and DSCP markings
- Deliver power to VoIP phones and access points
- Monitor port utilization and detect anomalies
This transforms the switch from a passive connectivity device into an active policy enforcement component of the SME network.
6. Wi-Fi Mesh and Centrally Managed Wireless Networks
Wireless connectivity is now the primary access method for employees, visitors, and IoT devices. Business-grade Wi-Fi mesh systems and managed access points provide:
- Seamless roaming across office spaces
- Centralized configuration and monitoring
- Multiple SSIDs mapped to VLANs
- Guest isolation and captive portal support
- Strong encryption (WPA3)
A professionally designed Wi-Fi layer directly influences employee productivity, customer experience, and operational reliability.
7. VoIP Telephony and Real-Time Communications
VoIP telephony has become a platform for:
- Customer service workflows
- CRM integration
- Call recording and analytics
- AI-assisted voice interactions
From a network engineering perspective, VoIP imposes strict requirements for low latency, minimal jitter, and controlled packet loss. Best practices include:
- Dedicated Voice VLANs
- QoS prioritization on switches and firewall/router
- Bandwidth reservation on WAN links
- Security controls for SIP/RTP traffic
Failure to address these requirements results in degraded call quality and reputational harm.
8. Reference SME Network Architecture
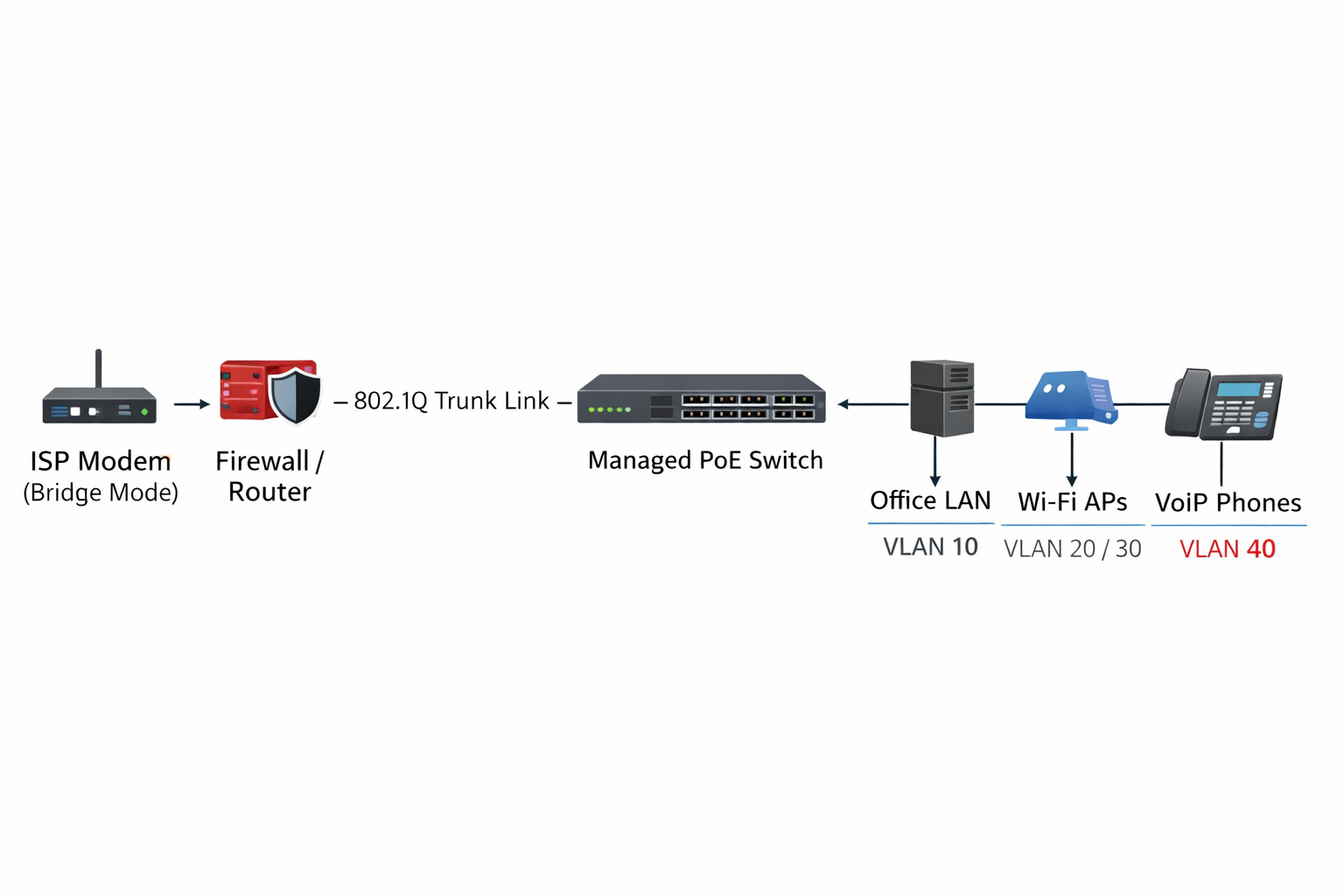
A representative SME architecture integrates the components discussed:
[ ISP Modem (Bridge Mode) ] | [ Firewall / Router ] | 802.1Q Trunk Link | [ Managed PoE Switch ] | | | Office LAN Wi-Fi APs VoIP Phones VLAN 10 VLAN 20/30 VLAN 40
This modular architecture supports incremental growth, simplifies troubleshooting, and aligns network design with business functions.
9. Network Management as an Operational Capability for SMEs
9.1 From One-Time Setup to Ongoing Network Operations
For many SMEs, network infrastructure is deployed as a one-time project rather than managed as a continuous operational capability. This “install-and-forget” approach leads to gradual degradation of performance, growing security gaps, undocumented configuration changes, and fragile VoIP and Wi-Fi performance. In contrast, professional network management treats the SME network as a living digital system that must be monitored, maintained, measured, and continuously improved.
Network management encompasses the coordinated processes, tools, and practices used to operate, secure, and optimize the network over its lifecycle. In the proposed SME architecture, network management becomes as important as the physical design of the bridged modem, firewall/router, managed switches, Wi-Fi mesh, and VoIP systems.
9.2 Core Functions of SME Network Management
A professional network management framework for SMEs includes the following core operational functions:
a) Monitoring and Observability
Continuous visibility into network health is essential. Key metrics include:
- WAN latency, jitter, and packet loss
- Firewall throughput and session counts
- Switch port utilization and error rates
- Wi-Fi client density, roaming performance, and interference
- VoIP call quality indicators (MOS scores, packet loss, jitter)
Real-time monitoring enables early detection of congestion, misconfiguration, and service degradation before these issues impact business operations.
b) Configuration and Change Management
Network configurations evolve as SMEs add users, devices, access points, and cloud services. Controlled change management includes:
- Centralized configuration backups of firewall, switches, and Wi-Fi controllers
- Versioning and documentation of network policies (VLANs, firewall rules, QoS profiles)
- Approval workflows for changes affecting VoIP, VPNs, or security posture
This reduces the risk of outages caused by ad-hoc configuration changes.
c) Performance Management and Capacity Planning
Professional network management uses historical data to anticipate growth:
- WAN bandwidth utilization trends
- Growth in VoIP endpoints and concurrent calls
- Wi-Fi client growth and peak usage patterns
- Cloud application traffic growth
Capacity planning allows SMEs to scale infrastructure proactively rather than reactively, avoiding performance bottlenecks during business expansion or seasonal demand peaks.
d) Fault Management and Incident Response
Structured incident management improves Mean Time to Repair (MTTR):
- Automated alerts for link failures, device outages, and service degradation
- Runbooks for common incidents (WAN outage, VoIP failure, Wi-Fi degradation)
- Root cause analysis and post-incident reviews
This professionalizes IT operations and reduces downtime.
e) Security Operations Integration
Network management and cybersecurity operations must be integrated:
- Correlation of firewall logs, intrusion alerts, and endpoint signals
- Detection of anomalous traffic patterns (e.g., command-and-control activity, lateral movement)
- Rapid containment of compromised segments using VLAN isolation
This operational integration supports a defense-in-depth security posture.
9.3 Network Management for VoIP and Real-Time Services
VoIP and video conferencing are highly sensitive to network conditions. Network management for real-time services includes:
- Continuous monitoring of latency, jitter, and packet loss
- Automated QoS validation to ensure voice traffic is prioritized
- Alerting when MOS scores fall below acceptable thresholds
- Capacity planning to ensure sufficient WAN bandwidth during peak call volumes
By operationalizing VoIP quality monitoring, SMEs can maintain consistent customer experience and service reliability.
9.4 Governance, Documentation, and Compliance
Network management is not purely technical; it is also a governance function. SMEs increasingly face data protection, audit, and contractual compliance requirements. Professional network management includes:
- Network architecture documentation and topology diagrams
- Asset inventories of network devices and connected endpoints
- Policy documentation for access control, remote access, and guest Wi-Fi
- Change logs and audit trails for configuration changes
This governance layer supports compliance with data protection and cybersecurity regulations applicable in India, Canada, the UK, and the USA.
9.5 The Role of KeenComputer.com in Managed Network Operations
KeenComputer.com provides SMEs with Managed Network Services (MNS) that operationalize the architecture proposed in this paper. These services typically include:
- 24/7 monitoring of firewall, switches, and Wi-Fi infrastructure
- Proactive firmware updates, patch management, and vulnerability remediation
- Performance optimization for WAN, Wi-Fi, and VoIP
- SLA-driven incident response and escalation
- Quarterly network health reviews and capacity planning workshops
- Documentation, asset management, and change governance
By outsourcing network operations to a specialized partner, SMEs gain enterprise-grade network management capabilities without the cost of building an internal IT operations team.
9.6 Network Management as a Strategic Enabler of Digital Transformation
Well-managed networks are a prerequisite for advanced digital initiatives, including:
- Cloud migration and SaaS adoption
- AI-powered customer service and analytics platforms
- Secure remote work and branch office connectivity
- IoT deployments in retail, manufacturing, and logistics
Network management thus becomes a strategic enabler of digital transformation, ensuring that the underlying connectivity layer does not constrain innovation or growth.
10. Business Impact and Return on Investment
Professional SME network design delivers tangible business outcomes:
|
Dimension |
Impact |
|---|---|
|
Security |
Reduced breach probability |
|
Reliability |
Higher uptime and service continuity |
|
Customer Experience |
Improved VoIP call quality |
|
Productivity |
Faster access to cloud tools |
|
Scalability |
Support for growth and AI adoption |
Empirical industry studies indicate that reductions in downtime and security incidents alone can offset network modernization costs within 6–12 months.
11. Future Outlook: SME Networks in the AI Era
Future SME networks will increasingly adopt:
- Cloud-managed networking platforms
- Zero Trust architectures
- AI-driven monitoring and anomaly detection
- Wi-Fi 6/7 for high-density environments
- Secure Access Service Edge (SASE) models
A modular, segmented network architecture provides a future-proof foundation for these evolutions.
12. Conclusion: From Network Design to Network Operations Excellence
While sound network architecture (bridged modem, firewall/router, managed switches, Wi-Fi mesh, and VoIP-ready design) provides the structural foundation for SME digital infrastructure, professional network management ensures that this foundation remains reliable, secure, and aligned with evolving business needs. SMEs that combine modern network design with ongoing cybersecurity and managed network operations—delivered through partners such as KeenComputer.com—transform IT from a fragile support function into a resilient operational platform for growth, innovation, and customer experience excellence.
.
References
- Behl, A., & Behl, K. (2017). Cyberwar: The Gray Zone. Oxford University Press.
- Cisco. (2023). Small Business Network Design Guide. Cisco Systems.
- NIST. (2020). Zero Trust Architecture (SP 800-207). National Institute of Standards and Technology.
- Tanenbaum, A. S., & Wetherall, D. (2021). Computer Networks (6th ed.). Pearson.
- Olifer, N., & Olifer, V. (2005). Computer Networks: Principles, Technologies and Protocols. Wiley.
- Cisco. (2022). VoIP Design and QoS Best Practices for Small Enterprises.
- Fortinet. (2023). Unified Threat Management for SMEs.
- IEEE. (2021). 802.11ax/6 Wireless LAN Standards Overview.
- ITU-T. (2020). QoS Requirements for IP Telephony.
- ENISA. (2023). Cybersecurity for SMEs. European Union Agency for Cybersecurity.
- NIST. (2018). Framework for Improving Critical Infrastructure Cybersecurity.
- ISO/IEC 27001:2022. Information Security Management Systems.
- Cisco. (2023). Network Management Best Practices for Small and Medium Businesses.
- Tanenbaum, A. S., & Wetherall, D. (2021). Computer Networks (6th ed.). Pearson.
- ITU-T G.114. (2020). One-Way Transmission Time for Voice Traffic.
- ENISA. (2023). Cybersecurity and Resilience for SMEs
